SCIM (System for Cross-domain Identity Management) is a standard for automating the exchange of user identity information between identity domains, or IdP systems. For example, as a company adds and removes employees from Okta, they are dynamically added and removed from Tracker. Though SCIM has only been verified and tested with Okta, it can be enabled for any IdP that supports SCIM and that’s also had SAML SSO configured with Tracker.
Features
Pivotal Tracker supports the following SCIM features:
- Create Users
- Update User Attributes
- Deactivate Users
Requirements
A Pivotal Tracker account needs to meet the following requirements:
- The account must be on an enterprise plan.
- The account must use SAML for SSO.
- Send an email to support@pivotaltracker.com requesting SCIM enablement.
Step-by-Step Configuration Instructions
Start by generating your SCIM token in Tracker
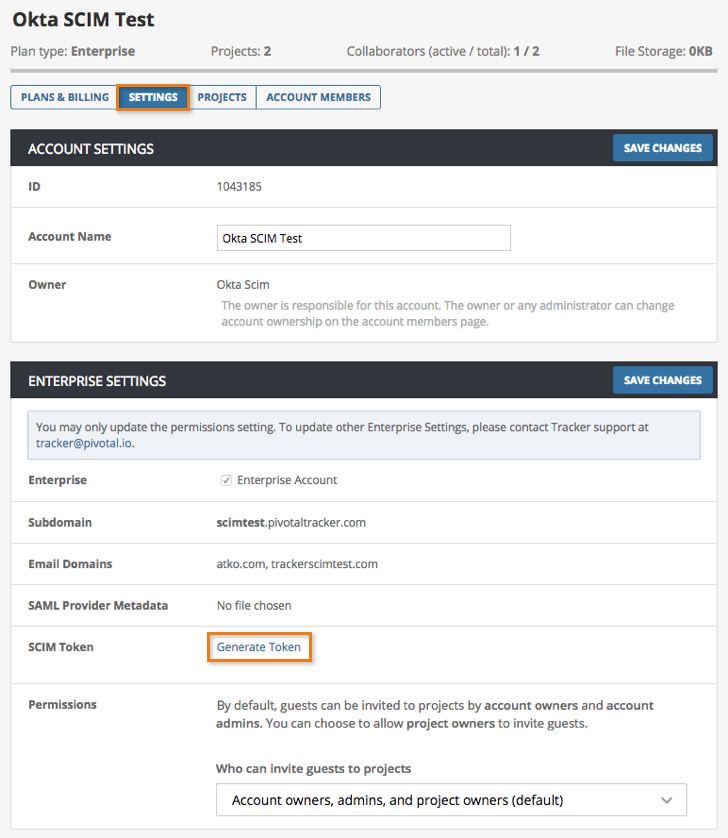
- An account owner or admin should visit their Account Settings page.
- Under the Enterprise Settings section, select the Generate Token link to the right of SCIM Token.
- The token generated will only appear once, and will not be visible after a page refresh (however, there will always be an option to re-generate the token).
Enable Provisioning for your Pivotal Tracker app in Okta
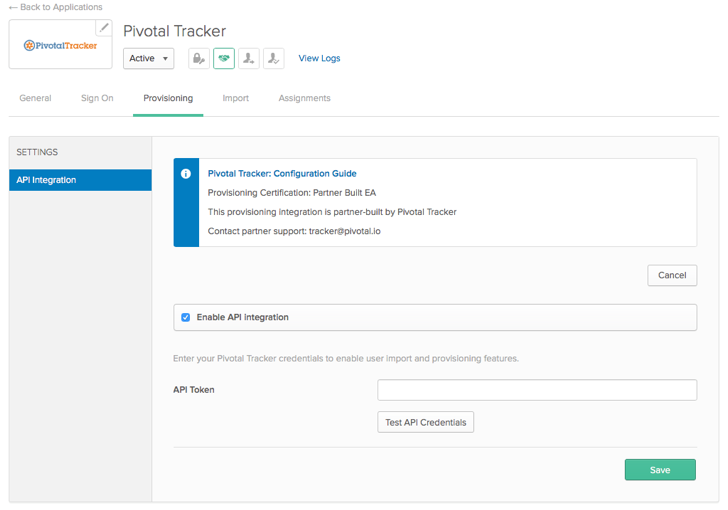
- Access your Pivotal Tracker app in Okta, which was previously added when SAML SSO was configured.
- Select Provisioning from the top menu, then select API Integration from the navigation sidebar. Select the Enable API Integration checkbox.
- Paste the SCIM token you retrieved from your Tracker Account Settings page into the API Token field.
- Select Test API Credentials to ensure the integration is working properly, then click Save.
Notes
Deprovisioning/deactivating users
When users are deprovisioned in Okta, a request is made in Tracker to flag the user for suspension. This means that the user will remain in Tracker for 30 days, and gives a time buffer in case the user was deprovisioned by mistake. Even though the user will still be visible in the Account Members list, the user will not be able to access Tracker as long as they’ve been deprovisioned in Okta. However, should they be reprovisioned in Okta, they will be able to access Tracker normally as long as it’s within the 30 day window.
At the end of 30 days, the user will be permanently suspended and removed from your Account Members list. You can also manually remove them from your Account Members list prior to the 30 day window by following the steps in Removing an account member.
Authorized/trusted domain(s)
Before Okta users can begin using SCIM with Tracker, they must be on an Enterprise plan and have their company domain(s) whitelisted to be authorized to use this feature. If your domain(s) have not yet been authorized to use Enterprise features such as SCIM, an error will be returned for users in Okta. If you’re on an Enterprise plan and are receiving an error, please contact our support team (support@pivotaltracker.com).